Security for Cyber-Physical Systems
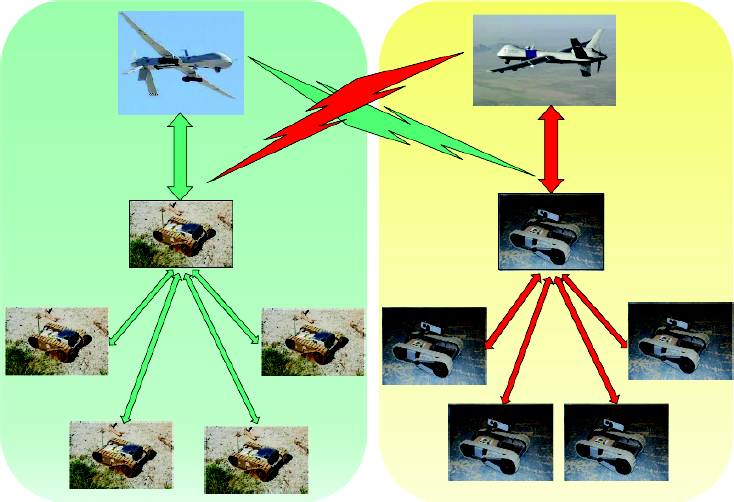
Secure communication is an essential requirement in networked cyber physical systems; especially, teams of autonomous vehicles and robots deployed by the army in combat scenarios. The decentralized nature of wireless mobile ad hoc networks makes them vulnerable to security threats. Unauthorized intrusion of such kind has started a race between engineers and the hackers; therefore, we have been witnessing a surge of new smart systems aiming to secure modern instrumentation and software from unwanted exogenous attacks. Our research aims to understand the fine interplay between the constraints in the mobility and communication capability under resource constraints such as onboard energy and available bandwidth, among teams of autonomous agents engaged in adversarial interaction over the communication channel.
|
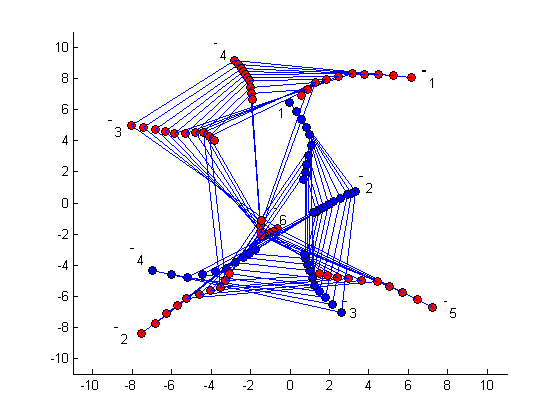
In this article, we study the problem of power allocation in teams of mobile agents in a conflict situation. Each team consists of two agents who try to split their available power between the tasks of communication and jamming the nodes of the other team. The agents have constraints on their total energy and instantaneous power usage. The cost function is the difference between the rates of erroneously transmitted bits of each team. We present a 2-level game formulation: At the higher level, the agents solve a continuous-kernel power allocation game at each instant. Based on the communications model, we present sufficient conditions on the physical parameters of the agents for the existence of a Pure Strategy Nash Equilibrium for the continuous-kernel power allocation game. At the lower level, we have a zero-sum differential game between the two teams and use Isaacs’ approach to obtain necessary conditions for the optimal trajectories. The optimal power allocation scheme obtained at the upper level is used to solve the lower level differential game. This gives rise to a games-in-games scenario which is one of the first such phenomena documented in the literature. |
|
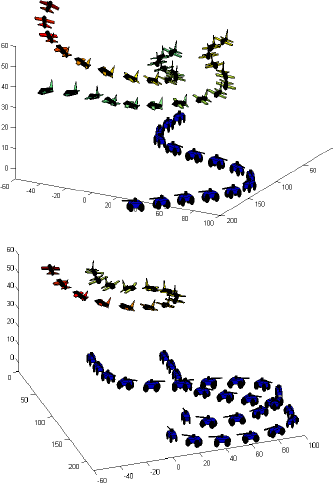
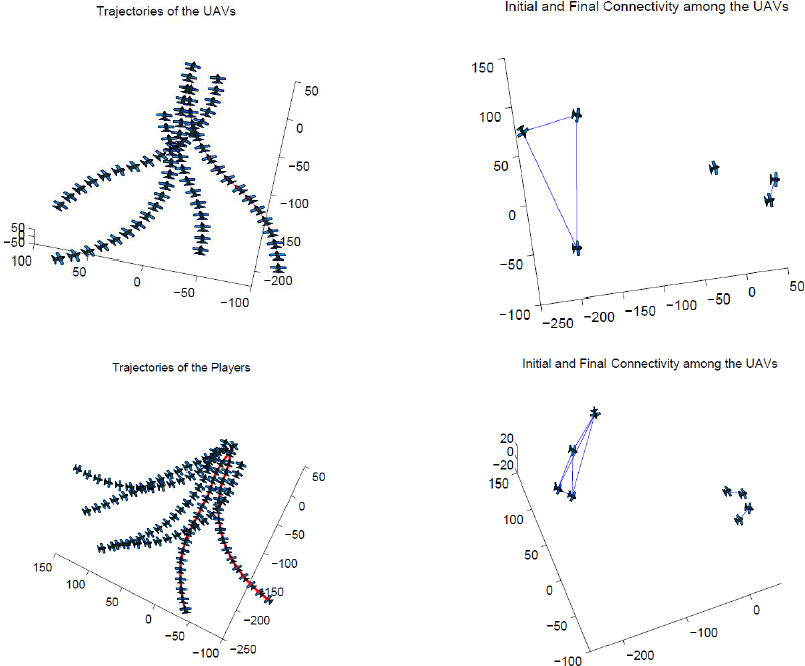
In this paper, we address the problem of jamming in a communication network within a team of mobile autonomous agents. In contradistinction with the contemporary research regarding jamming, we model the intrusion as a pursuit-evasion game between a mobile jammer and a team of agents. First, we consider a differential game-theoretic approach to compute optimal strategies for a team of UAVs trying to evade a jamming attack initiated by an aerial jammer in their vicinity. We formulate the problem as a zero-sum pursuit-evasion game, where the cost function is the termination time of the game. We use Isaacs' approach to obtain necessary conditions to arrive at the equations governing the saddle-point strategies of the players. We illustrate the results through simulations. Next, we analyze the problem of jamming from the perspective of maintaining connectivity in a network of mobile agents in the presence of an adversary. This is a variation of the standard connectivity maintenance problem in which the main issue is to deal with the limitations in communications and sensing model of each agent. In our work, the limitations in communication are due to the presence of a jammer in the vicinity of the mobile agents. We compute evasion strategies for the team of vehicles based on the connectivity of the resultant state-dependent graph. We present some simulations to validate the proposed control scheme. Finally, we address the problem of jamming for the scenario in which each agent computes its control strategy based on limited information available about its neighbors in the network. Under this decentralized information structure, we propose two approximation schemes for the agents and study the performance of the entire team for each scheme. |
|
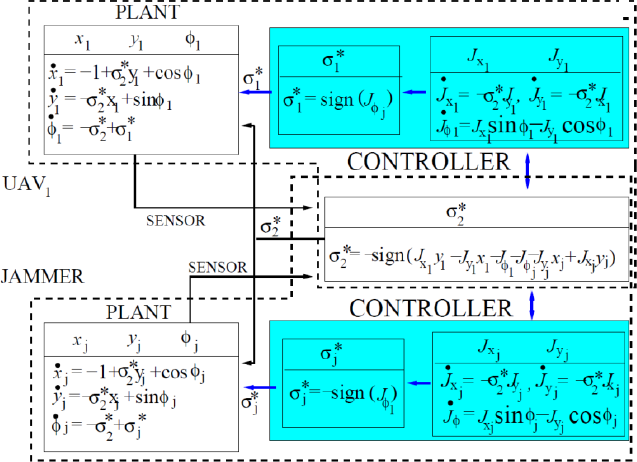
In this work, we address the problem of maintaining an operable communication link between two aerial vehicles in the presence of a jammer. In this work, we formulate the problem as a game of kind, and present the equations that characterize the barrier in the game using Isaacs' techniques. We derive the optimal control of the vehicles on the barrier, and present simulation results for specific terminal conditions. |
|
In this paper, we considered a differential game theoretic approach to compute optimal strategies by a team of UAVs to evade the attack of an aerial jammer on the communication channel. We considered two variants of the problem in this paper. We formulated the problem as a zero-sum pursuit-evasion game and used Isaacs' approach to derive the necessary conditions to arrive at the equations governing the saddle-point strategies of the players. The cost function was picked as the termination time of the game. We illustrated the results through simulations. |